YikYak Is Exposing Millions of User Locations
I was able to access the precise GPS coordinates (accurate to within 10-15ft) of all posts and comments on the YikYak platform, this leaves at least 2 million users at risk. This number is likely higher, as this user count is 6 months old.
I disclosed what I found to the YikYak team on April 11th 2022. Almost a month later on May 8th 2022 (1 day before public disclosure date), they responded by removing the user id being returned for posts and comments however this is not enough to protect privacy as it’s trivial to regain this information.
Edit (May 18th): YikYak has made what I consider substantial changes, more under the have things changed section.
Edit (May 11th): YikYak has made more changes detailed in the have things changed section.
Table of Contents
- What Is YikYak
- What Data Is Exposed
- How I Discovered It
- Data Visualization
- What Can YikYak Users Do To Protect Themselves?
- Takeaways
What is YikYak
YikYak is a pseudonymous messaging board, where users can see posts within a radius of 5 miles. Each user has an emoji and color to distinguish individuals, these can be reset if the user chooses. This feature allows conversation chains to continue in comment sections where users can interact.
Each post has a location associated with it by design, and when viewing a post the app displays how far away they are from you. The main target audience for YikYak is college students on college campuses.
What Data Is Exposed
- On All Posts & Comments
- Precise GPS Coordinates (accurate to within 10-15 ft)
- A user id (persistent across posts even if a user resets their avatar)
- After YikYak’s update on May 8th it takes maybe a few minutes of guessing to get this data back by manipulating the graphql query
Why It’s a Problem
Location data itself isn’t problematic for an app like this, it is problematic when the precise GPS coordinates are sent to the client and user ids are exposed. Combining these two pieces of information it is possible to de-anonymize users, since people are more likely to use their phones thus YikYak at home it’s possible to figure out the area where a user lives within 10-15 feet. This ability to de-anonymize is much more of a risk in low density rural areas where detached single-resident buildings are more than 10-15 feet apart, as a single GPS location narrows down a user to one address.
Since user ids are persistent it’s possible to figure out a user’s daily routine of when and where they post YikYaks from, this can be used to find out the daily routine of a particular YikYak user.
A non-exhaustive list of what a malicious actor could do with GPS data
- Break into a building when they know a YikYak user is somewhere else (on vacation or just not home)
- Stalk YikYak users by tracking the GPS location of their posts
- Unlawfully surveil and monitor users
Mitigations Recommended
In my email to the YikYak team I recommended some fixes they could implement in order to increase anonymity. I’ve ordered them from in my opinion what’s the most effective to the least effective.
- Truncate the GPS coordinate to only use a few decimal places such as 2 or 3, as this makes the location inaccurate to 0.6 miles or 300 feet respectively according to Wiki GIS.
- Change the API to calculate the distance from the client server-side, so that GPS coordinates are never sent to the client.
- Don’t display how far the poster is from the client, or just randomly generate how far away people are from each other.
- Don’t return user ids to the client when querying for posts/comments.
The most logical and efficient way to protect user privacy is to implement option number one, as this destroys the information ensuring nobody is ever able to recover the exact location again. The other options leave de-anonymization of users possible through other means. Despite this, on May 8th 2022 YikYak decided to go with option four after nearly a month to prepare for public disclosure.
YikYak’s Response
YikYak sent this a few days after my initial disclosure email to them.
We’re working on fixes to stop exposing user IDs to clients and soften how location is exposed
They then asked me to push back my initial disclosure date another 2 weeks to May 9th 2022, which I agreed to.
Have Things Changed
As of writing on May 9th things have not significantly changed. YikYak responded by removing the user id field being returned for posts and comments however this is not enough to protect user privacy. It’s still fairly trivial to access this information and would take only a few minutes to guess and check.
YikYak released a “Summer Spaceship” feature which allows users to save a GPS location and act as if they’re at that location when posting and viewing content on the app. This feature could allow for users who care about their privacy to set their location to be in a busy place to protect their anonymity. However, it does not appear that this feature is meant to protect user privacy and the branding around this feature does not reflect that this was the intention of the feature.
Edit May 18th: YikYak has rounded all GPS coordinates sent to the client, as well as the distances to various users. This is what I suggested to them, I’m assuming that the coordinates are only rendered server-side which is an improvement. Since the information isn’t destroyed, it is possible that some attack in the future could leave the exact coordinates exposed. Despite this, I’m glad that they finally changed things and the app is more secure for the privacy of individual users.
Edit (May 11th): YikYak has released version 1.4.3 which does calculate the distance to each post in feet, however since this is not rounded it’s still possible for trilateration the location of the post. Furthermore, it is still possible to get the user ID and exact location based on the API requests of older versions. This could be temporary to provide backwards compatibility with older versions of the app. If YikYak did take this more seriously they would restrict these fields from being returned and break older versions and force users to upgrade to a newer version of the app.
How I Discovered This
I intercepted the HTTP requests from the app by using mitmproxy, next I wrote some code that pretended to be the YikYak app to extract information from it. I then realized that YikYak was exposing the precise GPS coordinates of every poster and commenter to the client, which is when I started drafting up an email to YikYak and collecting some GPS coordinates to visualize some data.
Aside: If you want to learn how to intercept information like what this article is about, I’m working on a free YouTube series on David Teather Codes that will teach you how! So please subscribe, if that’s not your thing I’ve got a lot more content planned.
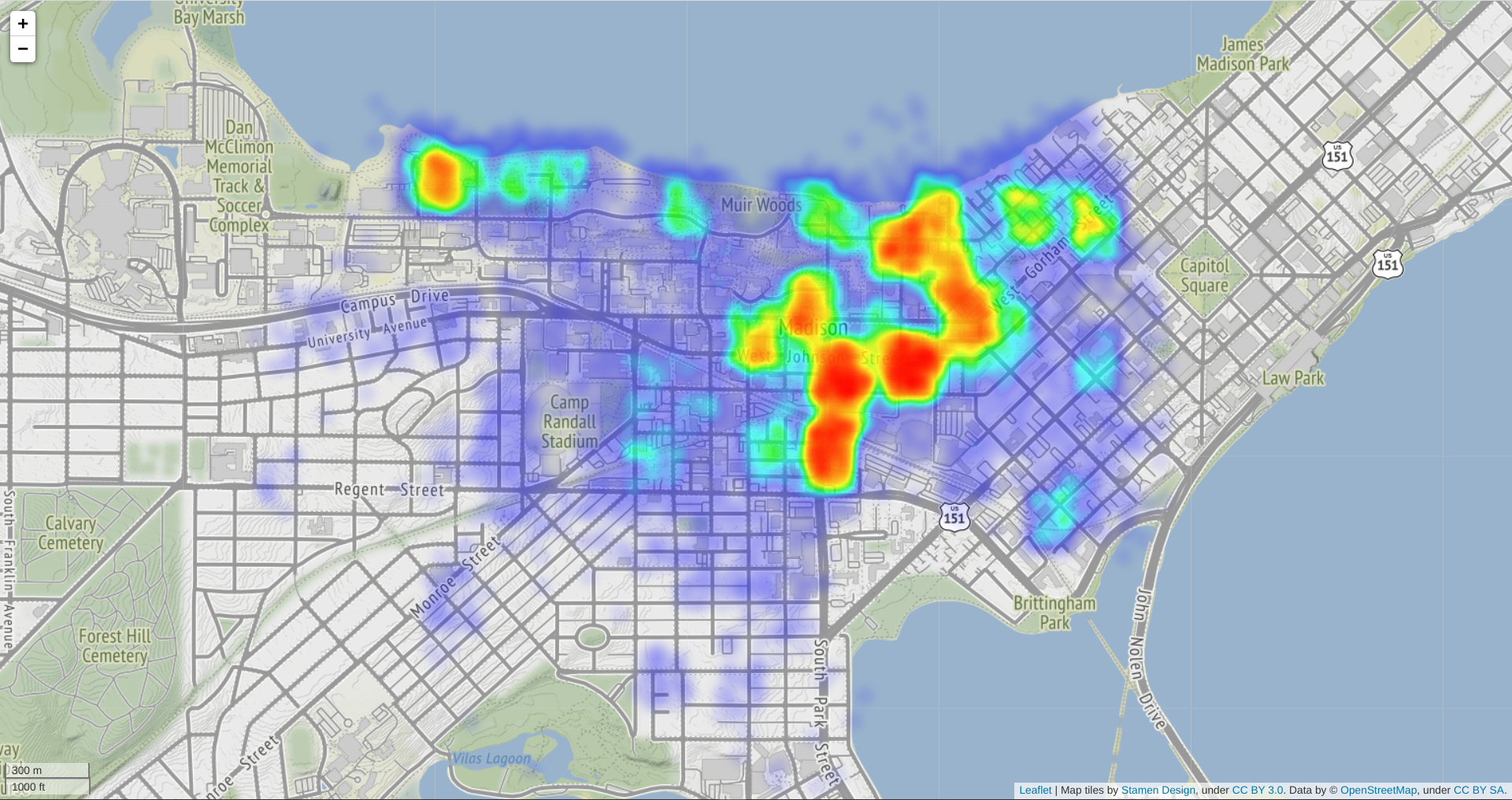
Data Visualization
I collected some of the exposed user data for a short amount of time after the disclosure to YikYak. I figured it would be a waste not to share a cool looking visualization.
Note: I’ve taken steps to protect the privacy and safety of YikYak users.
- Randomized GPS Coordinates
- Restricted the radius of visualized points to only include high density blocks, so that individual points cannot be pinned to a particular address
What The Data Tell Us
- College students use YikYak the most
- Student dorms and libraries are the “hottest” areas
- Not much else to be honest
What Can YikYak Users Do To Protect Themselves?
Don’t use YikYak in a place where you wouldn’t broadcast your GPS coordinates to strangers.
If this isn’t a sacrifice you’re willing to make, YikYak introduced a “summer spaceship” feature which allows you to save your GPS location and act as if you were at that location. You could set this location to be in a public place like a campus union, so that it’s harder to de-anonymize you. I haven’t done my own analysis to see if this hides your actual GPS location, but if implemented properly it would let you mask your actual location, thus protecting your privacy.
Takeaways
- “Anonymous” messaging apps don’t exist
- Apps we use without thinking may be putting us at risk to malicious actors, when we have little knowledge or control over how securely our information is stored
- If you’re designing an app that sends sensitive information to a client, it’s best to not send it at all and when possible anonymize it
Hope you enjoyed :)
If you enjoyed consider subscribing
Check out my Twitter or my other socials